Wi-Fi has become an indispensable part of our daily lives, connecting our devices seamlessly to the internet. But have you ever wondered how a device, such as your smartphone or laptop, connects to a Wi-Fi access point? In this blog post, we’ll dive into the initial communication process that occurs between a Wi-Fi device and an access point, helping you understand how your devices establish a secure and reliable connection.
We’ll explore each step of the Wi-Fi handshake, the roles played by the device and access point, and how they ensure a secure connection. This guide will cover the essential components of Wi-Fi initial communication, including association, authentication, and data transmission setup.
How Does Wi-Fi Communication Start?
Wi-Fi communication between a device (often called a station) and an access point (AP) involves a series of steps to establish a secure, high-quality link. The main stages of this communication process are:
- Beacon Frame Transmission
- Probing and Discovery
- Authentication
- Association
- Security Handshake
Each of these steps plays an important role in ensuring that the connection between the device and the access point is robust and secure.
Step 1: Beacon Frame Transmission
The communication between a Wi-Fi device and an access point begins with the access point periodically broadcasting beacon frames. These beacon frames are like announcements, letting devices know that the access point is available and ready to provide a connection.
A beacon frame contains important information about the network, such as:
- SSID (Service Set Identifier): The network name.
- Supported Data Rates: The speeds that the access point can provide.
- Encryption Information: Details about the security protocols used (e.g., WPA2, WPA3).
These beacon frames allow nearby devices to detect the presence of Wi-Fi networks and decide which one to connect to.
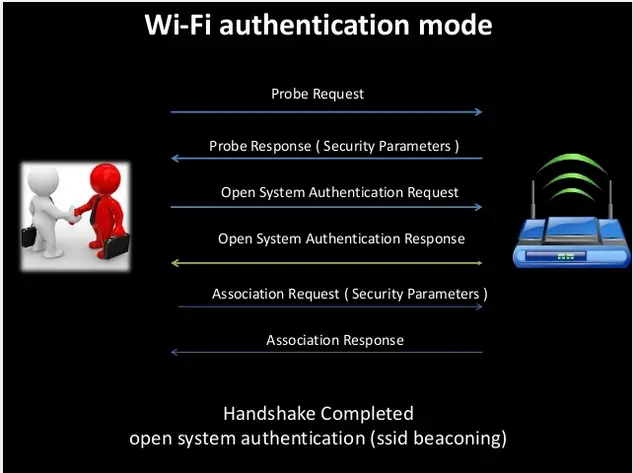
Step 2: Probing and Discovery
When a Wi-Fi device wants to connect, it sends a probe request. This request allows the device to discover available access points and collect information on network capabilities.
The access point then responds with a probe response, containing details such as the supported data rates and encryption types. This process allows the device to select the best access point based on signal strength, capabilities, and security requirements.
Step 3: Authentication
Once the device has selected an access point, the next step is authentication. Authentication is the process of verifying that the device is authorized to connect to the access point. Initially, this process is often open authentication, where the device simply asks to connect, and the access point responds.
In modern Wi-Fi networks, authentication is typically enhanced by security protocols such as WPA2 or WPA3, which use cryptographic methods to ensure that only authorized devices can connect.
For instance, with WPA2 or WPA3, authentication may involve a pre-shared key (PSK) or a more advanced EAP (Extensible Authentication Protocol) mechanism, which ensures that both the device and the access point can validate each other.
Step 4: Association
After successful authentication, the device proceeds to the association stage. In this stage, the device sends an association request frame to the access point, which includes specific information like:
- Supported Data Rates: Capabilities of the device.
- SSID: The specific network the device wants to connect to.
The access point then responds with an association response frame, which includes an Association ID (AID). This AID is used to identify the device within the network. Once associated, the device is officially connected to the network, allowing data to be exchanged.
Step 5: Security Handshake
For secure communication, a four-way handshake is performed to establish encryption keys that will be used to encrypt the data exchanged between the device and the access point. This step ensures that the data remains confidential and protected from eavesdropping.
In WPA2 and WPA3 networks, the four-way handshake generates a Pairwise Transient Key (PTK), which encrypts the communication. This step is crucial for ensuring that any data transmitted over the network is secure.
Data Transmission
After the device has successfully completed the authentication, association, and security handshake steps, it can now begin data transmission. The device and access point can exchange data, with frames containing payloads that are encrypted using the agreed-upon keys.
At this point, the connection is fully established, and the device is free to send and receive data over the Wi-Fi network.
Common Issues During Wi-Fi Connection
- Weak Signal Strength: If the access point’s signal is weak, the initial beacon may not be received properly. Ensure that the device is within range of the access point.
- Authentication Failures: Incorrect passwords or mismatched security settings can prevent successful authentication.
- Interference: Interference from other electronic devices or Wi-Fi networks can cause delays or failures in communication. Changing the Wi-Fi channel can help reduce interference.
Why Understanding Wi-Fi Communication Is Important
Understanding how Wi-Fi devices communicate with access points helps:
- Troubleshoot Issues: Identifying where the connection process is failing allows you to solve problems effectively.
- Optimize Network Performance: Knowing how devices select access points and authenticate helps you optimize the layout of access points to ensure maximum coverage and minimal interference.
- Enhance Security: Understanding the security handshake process helps in choosing the right security settings to keep the network safe from unauthorized access.
Conclusion
The initial communication between a Wi-Fi device and an access point involves several key steps, from discovering the network to establishing a secure connection. Each stage, including beacons, probing, authentication, association, and security handshakes, plays a crucial role in ensuring a smooth and secure Wi-Fi experience.
By understanding these stages, you can troubleshoot connection problems, optimize your Wi-Fi network, and ensure your data remains secure. The next time your device connects to a Wi-Fi network, you’ll know exactly what happens behind the scenes!