Secure boot requires each an every operating system software to be signed with unique key to build the trust from top to bottom among the software. When your machine’s Ubuntu is enabled with UEFI Secure boot, the loading of third party / unknown kernel modules are prevented by default, because the running kernel has EFI_SECURE_BOOT_SIG_ENFORCE enabled in its kernel configuration.
So, if we want to load some kernel module, then the verify first thing we would need is to make sure it is signed. To begin with signing kernel module for UEFI Secure Boot Ubuntu, we need to create a X509 certificate that can be imported in firmware. Using OpenSSL we can certificate for use in UEFI Secure Boot.
First lets defined the configuration file as,
$ vim openssl.conf# This definition stops the following lines choking if HOME isn't
# defined.
HOME = .
RANDFILE = $ENV::HOME/.rnd
[ req ]
distinguished_name = req_distinguished_name
x509_extensions = v3
string_mask = utf8only
prompt = no
[ req_distinguished_name ]
countryName = CA
stateOrProvinceName = Quebec
localityName = Montreal
0.organizationName = cyphermox
commonName = Secure Boot Signing
emailAddress = example@example.com
[ v3 ]
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid:always,issuer
basicConstraints = critical,CA:FALSE
extendedKeyUsage = codeSigning,1.3.6.1.4.1.311.10.3.6,1.3.6.1.4.1.2312.16.1.2
nsComment = "OpenSSL Generated Certificate"Now, create public and private keys using openssl command as,
$ openssl req -config openssl.conf -new -x509 -newkey rsa:2048 -nodes -days 36500 -outform DER -keyout "MOK.priv" -out "MOK.der"This command, will create the “MOK.priv” and “MOK.der” files in present working directory (PWD) by accepting openssl.conf as input file.
Now, the next step is to enroll this keys with the SHIM UEFI Bootloader ( SHIM is a simple software package that is designed to work as a first-stage bootloader on UEFI systems ) . This enrolling can be done as,
$ sudo mokutil --import MOK.der
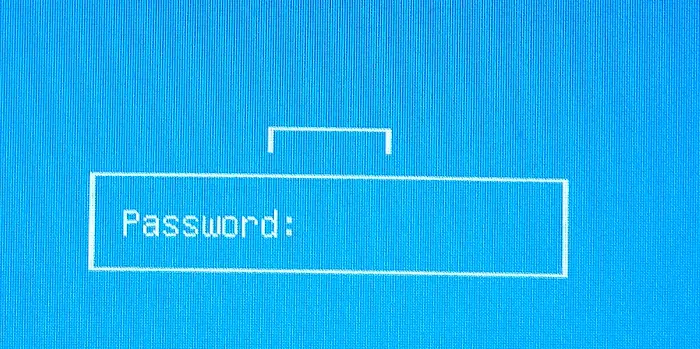
input password:
input password again:Remember the password, you entered here, as we would need to add this when we reboot the machine.
Now reboot the machine, and you will see the blue screen as below, during the next boot. The screen is of “Shim UEFI Key Management”
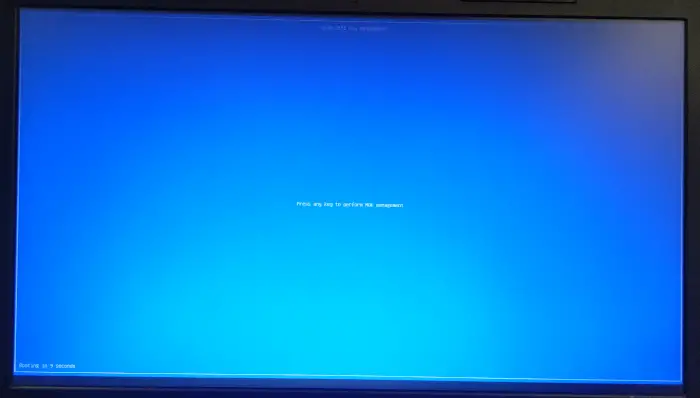
On this screen, press any key as suggested, and we will see the next screen as,
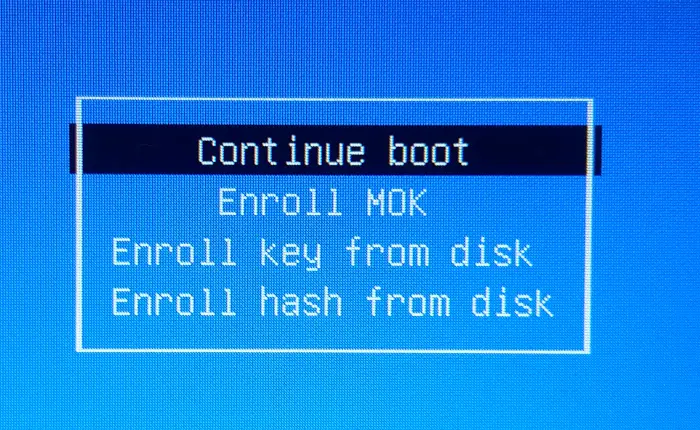
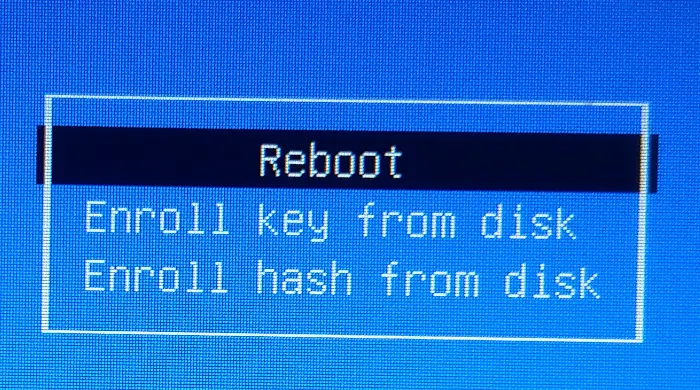
From this, select “Enroll MOK” and press enter, we will see the next screen asking for “Enroll the Keys” , there select “Yes” and go to next screen.
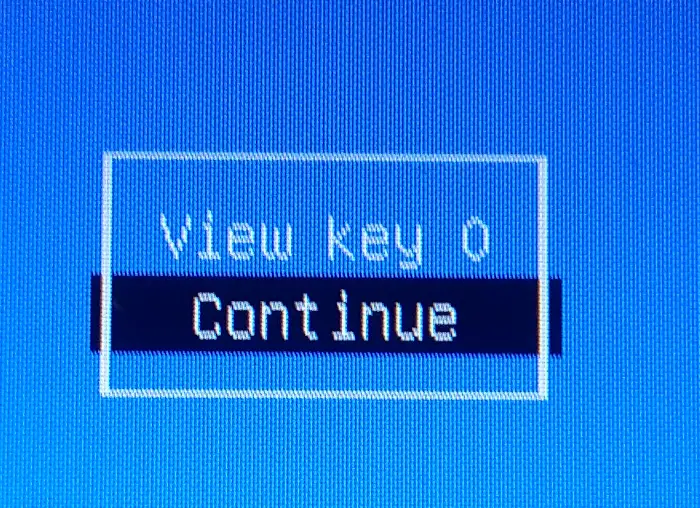
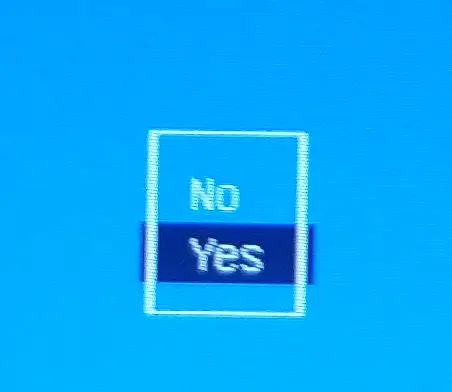
Now, after your Linux machine is rebooted completely, lets go back to signing the kernel module and try to insert it.
$ kmodsign sha512 MOK.priv MOK.der hello.koNow, if we try to insert this module,
$ sudo insmod hello.koThis worked without any error, and we can see the printk messages in dmesg as,
$ dmesg
[43103.294577] Hello, worldReference : https://ubuntu.com/blog/how-to-sign-things-for-secure-boot