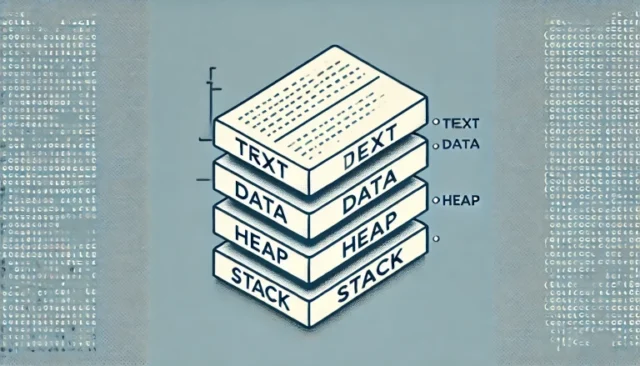
In C programming, understanding how memory is allocated is crucial for writing efficient and bug-free code. The memory layout of a C program consists of different segments, each serving a specific purpose in the program’s execution. These segments include Text, Data, Heap, and Stack, and each plays a unique role in how your program runs and manages memory.
This detailed guide will walk you through the memory layout of a C program, covering each segment—Text, Data, Heap, and Stack—to help you gain a deeper understanding of how your code interacts with memory at runtime.
Overview of Memory Segments in a C Program
A C program divides its memory into distinct segments, which include:
- Text Segment: Stores the compiled machine code of your program.
- Data Segment: Divided into initialized and uninitialized (BSS) sections for storing global and static variables.
- Heap Segment: Used for dynamically allocated memory at runtime.
- Stack Segment: Manages function calls, local variables, and control flow.
Understanding the role of each of these segments is crucial for efficient memory management and avoiding common issues like memory leaks and stack overflows.
1. Text Segment
The Text segment is a read-only section of memory that contains the compiled machine code of your program. It includes all the executable instructions generated from your source code. The text segment is typically read-only to prevent accidental modification of instructions during program execution, which also enhances security by avoiding malicious code injection.
- Characteristics:
- Contains program code and read-only data, such as string literals.
- Executable instructions are stored here.
- Usually marked as read-only by the operating system to prevent unintended changes.
Example: When you define a function in your C code, such as:
void greet() {
printf("Hello, World!\n");
}The compiled machine code for greet() resides in the text segment.
2. Data Segment
The Data segment is divided into two sections: initialized data and uninitialized data (BSS).
- Initialized Data Segment: Stores global and static variables that are explicitly initialized by the programmer.
- Example:
int x = 10;
static int y = 20;Variables x and y are stored in the initialized data segment.
- BSS (Uninitialized Data): Stores global and static variables that are not initialized.
- Example:
int z;
static int w;Variables z and w are stored in the BSS segment.
The data segment is writable, allowing modification of the variables during program execution.
3. Heap Segment
The Heap segment is used for dynamic memory allocation. Memory in the heap is allocated at runtime using functions like malloc(), calloc(), and realloc(). The heap is managed manually by the programmer, which means you are responsible for both allocating and freeing memory.
- Example of Heap Allocation:
int *ptr = (int *)malloc(sizeof(int) * 10);
if (ptr == NULL) {
printf("Memory allocation failed\n");
}In this example, memory for an array of 10 integers is allocated in the heap.
If the memory allocated on the heap is not properly freed using free(), it can lead to memory leaks. Proper memory management in the heap is essential for avoiding such issues.
4. Stack Segment
The Stack segment is used for function calls, local variables, and control flow. The stack operates in a Last In, First Out (LIFO) manner, meaning that the last function called is the first one to be completed.
- Characteristics:
- Stores function call frames, including local variables, return addresses, and function parameters.
- Memory is automatically managed—allocated when a function is called and deallocated when the function exits.
- Grows and shrinks as functions are called and return.
Example:
void calculate(int a, int b) {
int result = a + b;
printf("Result: %d\n", result);
}In the above example, the local variable result and parameters a and b are stored in the stack segment.
Stack Overflow: If too many function calls are nested or if excessive local variables are declared, the stack can overflow, leading to a program crash. This is common in programs with deep recursion.
Comparison of Heap and Stack
The Heap and Stack segments serve different purposes in memory allocation:
- Stack: Automatically managed by the compiler; used for local variables and function calls. Faster access but limited in size.
- Heap: Manually managed by the programmer; used for dynamic memory allocation. More flexible but can lead to memory leaks if not properly managed.
| Feature | Stack | Heap |
|---|---|---|
| Management | Automatically by compiler | Manually by programmer |
| Size | Limited, usually smaller | Larger, flexible size |
| Speed | Faster | Slower |
| Usage | Local variables, function calls | Dynamically allocated memory |
Best Practices for Memory Management in C
- Avoid Memory Leaks: Always use
free()to release memory allocated on the heap once it is no longer needed. - Initialize Variables: Initialize global and static variables to avoid undefined behavior.
- Minimize Recursion: Be cautious with deep recursion to prevent stack overflow.
- Use Valgrind: Tools like Valgrind can help detect memory leaks and other memory-related issues in your C program.
Conclusion
Understanding the memory layout of a C program—including the Text, Data, Heap, and Stack segments—is fundamental for writing efficient and error-free code. Each segment plays a critical role in the execution of your program, from storing executable code and global variables to managing dynamic memory and local function variables.
By understanding how memory is managed, you can avoid common pitfalls like memory leaks, stack overflows, and undefined behavior, ultimately leading to more reliable and efficient programs. Use this guide as a reference to enhance your skills in memory management and debugging in C programming.